Continuous Data Protection
Continuous data protection (CDP) empowers enterprise businesses today to have the confidence that their data can be recovered in the wake of cyberattacks, outages, natural disasters, or other failures.
What is CDP?
Making the Case for Continuous Data Protection
Continuous data protection enables all changes to be documented and minimizes data loss following cyberattacks, outages, or failures.
Data is perhaps the most valuable resource for businesses in the digital age.
Continuous data protection (CDP) empowers enterprise businesses today to have the confidence that their data can be recovered in the wake of cyberattacks, outages, natural disasters, or other failures. CDP is a real-time data backup strategy that saves and documents a copy of changes made to data, which enables files to be restored from different points in time.
This is important because it can help minimize data loss and protect against threats such as malware, ransomware, and accidental deletion. This level of real-time backup is paramount when considering the ever-evolving threat landscape and persistent malicious attacks from bad actors.
“IT leaders know that no amount of preparation is guaranteed to keep attackers out. Therefore, having absolute certainty of data survival and recovery in the face of any attack type is a requirement for any organization,” according to IDC’s Improving Data Resilience with a Cloud-First Approach report.
CDP creates a snapshot of data modifications and transaction that occurs in an enterprise, which then enables rapid recovery of data in the event it is lost, corrupted, or modified. This solves the problem of the backup window in which enterprise organizations are at risk of losing data created or modified between two scheduled backups.
Without CDP, if new data is created – and then lost or corrupted between scheduled backup windows – it might be unrecoverable. CDP lets enterprises capture an up-to-date copy of their information and allows data to be restored from different points in time.
Benefits
Benefits of Continuous Data Protection
Data protection has always been top of mind for organizations, but today’s businesses have amassed volumes of data that is at risk from growing threats. This requires an evolved approach to enable organizations with distributed data storage to have the same level of protection regardless of the system on which it resides.
And while it is impossible to prevent all attacks, it is critical organizations are able to remediate and recover from an attack or data breach. CDP takes up a critical role in this effort to enable a business to continue to operate by evaluating and testing clean points, standing up safe environments, recovering backed up data sets, and continually protecting and testing data in air-gapped instances. An important aspect of CDP is to leverage data awareness to proactively alert IT teams when threats arise.
With CDP in place, enterprises can achieve many benefits.
Reduced risk of data loss: Because CDP constantly collects updates, changes, or modifications as well as tracks new data, it is less likely that data will be lost during an event. The capture of transaction and associated date keeps a near-real-time record of data and reduces the risk of data loss.
Low recovery point objective: RPO is the maximum amount of data loss that can be tolerated after an unplanned incident, usually represented as a timeframe. Because CDP maintains an up-to-date copy of data, it is able to recover data rapidly in the event it is lost or corrupted.
Better data availability: With CDP, data is more easily accessible to those with the rights to use it. Critical systems and applications will be able to continue accessing data.
Faster recovery following attack: CDP can speed recovery times for a business that has suffered an attack. The up-to-date record of data will more quickly get systems and applications back to running smoothly.
Constant data syncing: Because CDP collects changes related to data, the data will be accurate when a system crashes and it needs to be recovered.
Version control: The capability makes it possible to save multiple versions of data and minimize any damage or deletion of data in the instance that another user is accessing the data.
Rollback options: Because CDP keeps data current, organizations can roll back to the desired version of data if there is an attack or other event.
CDP represents few downsides for enterprise organizations, but it can become a single point of failure, require an investment in physical disk storage, and increase load on data resources – unless businesses choose to invest in a cloud-based CDP offering.
Features
Cloud-Based Continuous Data Protection
CDP allows quick and comprehensive recovery of data, and when delivered via a cloud-based service, it also can empower businesses to secure data, anticipate risks, minimize data, and rapidly recover in the face of any threat.
Cloud-based data protection services mitigate the costs and risk of a single point of failure, while also providing enterprise organizations with a better data resilience posture that can accelerate recovery from ransomware, malware, or other malicious attacks. Cloud-based CDP providers can dedicate security specialists to protecting data and securing infrastructure as well as housing data in an off-site location, better protecting it from breaches and attacks.
CDP delivered via a cloud service also can provide centralized security and cost efficiencies. For instance, traditional CDP could require large, physical services that need to be installed, maintained, and updated by the IT team. With a cloud provider, data backups can be automated and cloud encryption can keep data in a read-only state that only authorized users can decrypt – which will protect data if a system is compromised.
Cloud offerings also can mean a lower upfront cost when investing in CDP and lower ongoing operational and maintenance expenses. With the promise of increased reliability and availability, cloud-based CDP can more easily scale and provide businesses with great flexibility.
“With these cloud resources and advanced software solutions, organizations can implement layered protection strategies that give it the best opportunity for fast, accurate recovery from cyberattack,” IDC says in its report. “As-a-service solutions, whether for backup, disaster recovery, or cyber-recovery, simplify those operations and leave the IT team time to pursue higher-value projects. By combining advanced cyber-resilience software and operations with cloud resources for storage and immutability, IT teams can take proactive measures to minimize the chances of a debilitating ransomware event.”
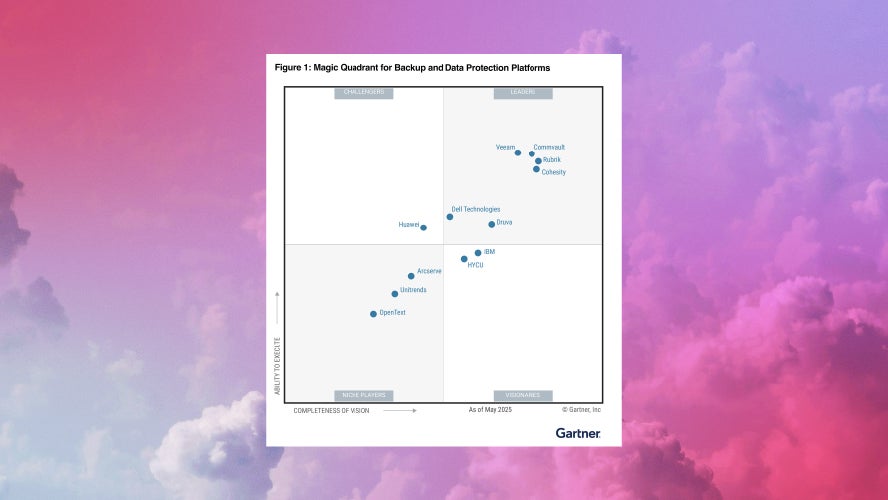
Gartner® Magic Quadrant™

Endpoint Data Protection: A Buyer’s Checklist
