The digital landscape is evolving. Cyberthreats have become more sophisticated, data estates are growing, and IT resources are shrinking. Today’s organizations need a more proactive approach to protecting their data in an ever-changing threat landscape. And while traditional data protection solutions may play a pivotal role in recovering post-attack, they are reactionary, narrowly focused, and no longer sufficient.
Cyberthreats today are designed to silently bypass perimeter defenses and inflict pain in ways that traditional backup and recovery solutions cannot combat. The threat of data exfiltration, theft, and damage is now more prevalent than ever and can be devastating to businesses if not addressed.
Proactive, Layered Data Protection
To address these cyber threats, organizations must look beyond conventional security tools and take steps to ensure data resiliency. This requires a proactive approach with layered protection, also known as defense in depth. It is the practice of implementing multiple tools and measures to protect against a wide range of threats. Each layer has a specific function, working in unison for multi-faceted protection for your environment. Commvault applies this very principle to data protection, uniquely delivering the right breadth of detection, security, and recovery capabilities to actively secure, defend, and recover data broadly across production and backup environments.
Layered protection that actively defends data and its recoverability across the industry’s
broadest set of workloads
Secure
Hardened, zero-trust, immutable architecture with built-in security controls to secure data, prevent unwanted access and data exposure, and drive compliance in the face of evolving cyber threats.
Defend
Patented early warning and in-depth monitoring to surface and neutralize zero-day and insider threats before they cause harm; containing breaches, limiting windows of exposure, and flagging malicious activity sooner to reduce recoveries.
Recover
Proactive and reliable recoverability across on-prem, cloud, and SaaS workloads proven to reduce downtime, prevent reinfection, and accelerate response times for unrivaled business continuity.
Innovative Data Protection with New
Products and Services
We are pushing the boundaries of data protection in this modern world, and redefining how businesses of every size combat risk, minimize threats, secure entire data estates, and drive better business outcomes. We are setting a higher standard for customers’ security posture and delivering the best value in data protection. New products and features include:
- Commvault Auto Recovery delivers complete cyber recovery and business continuity, both on-premises and in the cloud, providing secure, reliable, and near real-time cyber resiliency.
- Recovery orchestration with one-click recovery of clean copies across workloads to production after validating and sanitizing recovery points.
- Recovery validation to continuously validate backups, demonstrate recovery readiness, and reduce recovery testing complexities.
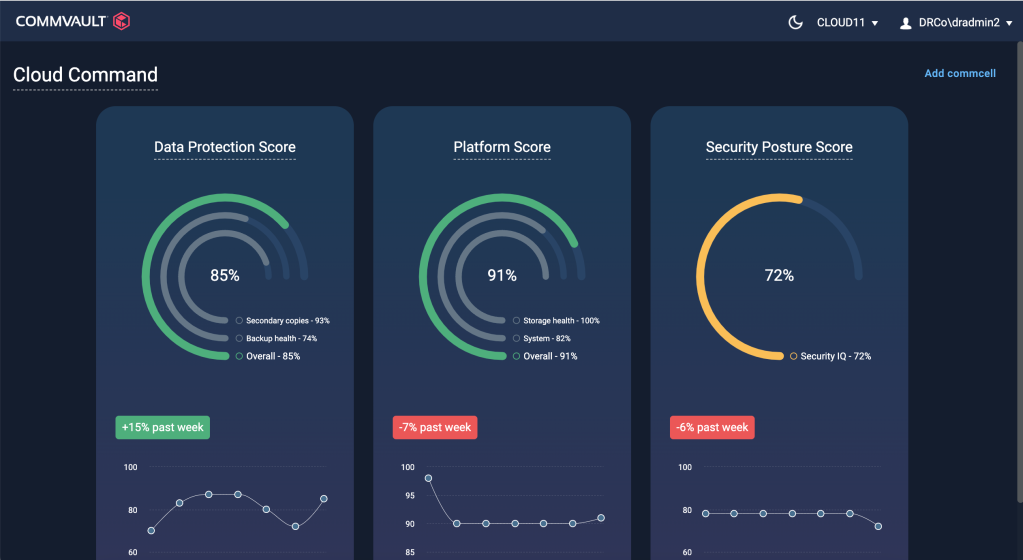
- Commvault Cloud Command provides customers global visibility and actionable insights across SaaS, cloud, and on-premises through a SaaS-delivered unified platform. It enables standardization of security postures and simplifies data risk management to make optimal decisions for recovery readiness.
- Commvault Risk Analysis identifies, categorizes, and classifies sensitive data such as personal, financial information, and intellectual property to prioritize security efforts and take action to reduce data exfiltration.
- Commvault Threat Scan allows organizations to scan backup content to identify malware and files that have been encrypted, corrupted, or significantly changed to recover clean data and avoid file reinfection.
- Security ecosystem expansion with bidirectional integrations with SIEM & SOAR platforms to meet compliance and improve your security posture by helping to align your response time through automatic actions.
- Dynamic Credential Management integration with CyberArk to minimize the risk of stored credentials for workload protection on demand, allowing organizations to securely manage credentials within CyberArk rather than within the backup environment.
- ThreatWise Advisor assesses backup environments and intelligently recommends decoy placement to further harden critical workloads and reduce the cognitive load for users.
Delivering a proactive and reliable recovery across the industry’s broadest workload coverage is proven to reduce downtime, thwart data loss, and accelerate response times. Businesses will benefit from our end-to-end insights and observability across the entire data protection lifecycle to anticipate risk, proactively minimize threats, control data (and its access), and drive more informed recovery outcomes.
Organizations of all sizes can feel confident that with the help of Commvault’s advanced data protection and recovery solutions, you can become the face of the next generation of data protection: Data, Secured. Data, Defended. Data, Recovered.
To learn more, use our buyer’s guide to map your current cyber security protection and recovery capabilities and determine how best to optimize your readiness plan across hybrid, cloud, or SaaS workload environments.
Watch our video on Data Protection Redefined as our mission is to secure, protect, and recover all your data with the world’s only unified data protection platform, which has the lowest TCO of any solution that even comes close.
Visit our web page to learn.


